Introduction
This section explains the best practices to apply when configuring EvoShield profiles to fully protect your server and applications from DDoS attacks.
What are EvoShield profiles?
EvoShield DDoS protection profiles are individual mitigation modules each designed to process the traffic being sent to a specific type of application or game server. Each profile implements full layer 7 stateful heuristic mitigation for the corresponding application, ensuring that only valid traffic from legitimate users is able to reach your applications. This fully comprehensive approach ensures that even the most sophisticated application layer attacks consisting of traffic which other DDoS protection systems and the application itself would consider to be valid are mitigated without impact to the server or application.
It is important to use the correct profile for each of your applications since the profile will not permit any traffic which is invalid in the context of a client to server connection for the specified application. This means that setting up a Garry's Mod profile for a Rust server would prohibit any users/players from connecting to the Rust server.
Configuration
The recommended approach is to setup an EvoShield profile for each of your server applications which are reachable on the internet and block all other traffic that doesn't match a profile. These are applications which listen on/bind to UDP and/or TCP port(s) that the corresponding client applications can then connect to. Examples include web servers such as Apache or Nginx, your SSH or RDP server, and any game server applications.
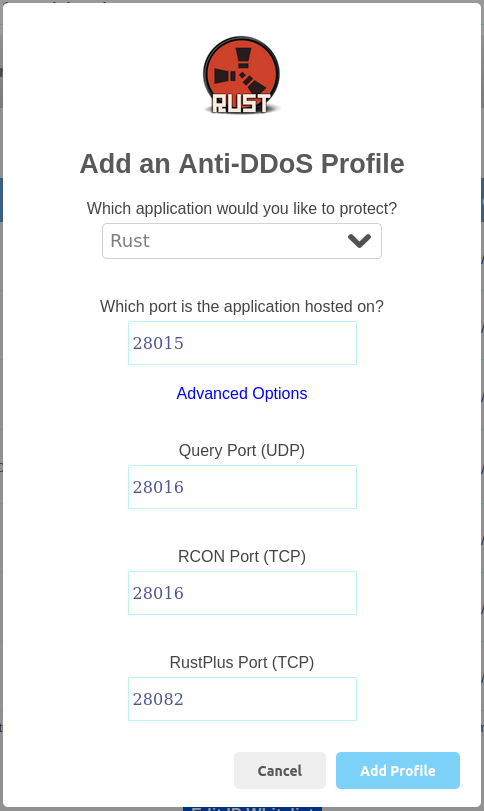
Adding Profiles
To setup a new profile, first click the Add a profile button.
You can then select the corresponding profile for the application that you would like to protect.
The port field will be pre-populated with the default port number for the application (when applicable). If your application is running on a different port, please adjust this field accordingly. When you click Add Profile, the EvoShield profile will instantly apply to inbound traffic destined for the specified port. In some cases it may take up to a few minutes for the changes to propagate, and the EvoShield profile will then be applied to inbound traffic from users in all regions.
To prevent actively connected users from disconnecting from the server, we recommend setting up EvoShield profiles before your users connect to the server, or during a server restart for example. Since EvoShield inspects the state of the connection in the context of the application, existing connections will be considered to be in an invalid state when the EvoShield profile is initially added.
Block inbound traffic that doesn't match a profile

When configured to block inbound traffic which does not match a profile, EvoShield will authorise all outbound traffic which originates from your server (such as DNS lookups and HTTP requests), as well as the inbound response to this traffic. All other inbound traffic will be blocked, such as traffic destined for ports (or protocols such as ICMP) that an EvoShield profile has not been setup on. This is the most effective configuration since it greatly reduces the available attack surface. This option is enabled at all times for EvoShield Remote DDoS Protection services and cannot be disabled, but is optional with VPS Hosting and VDS Hosting services.
Example Configurations
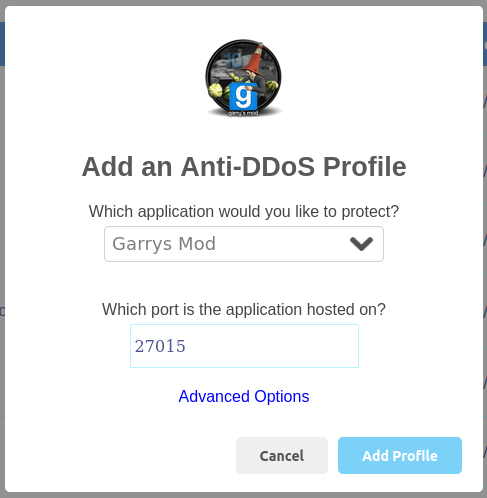
The following example is suitable for a Linux server with an SSH server on TCP port 22, as well as a Rust server and a Minecraft server running on the default ports. The server also hosts an Nginx web server on TCP ports 80 (HTTP) and 443 (HTTPS), and a MySQL database server to which remote access is required on TCP port 3306. The ICMP profile has also been setup to ensure that the server responds to ICMP traffic while still being protected from ICMP based DDoS attacks. The user has enabled Block inbound traffic that doesn't match a rule and as such, all other inbound traffic will be discarded.
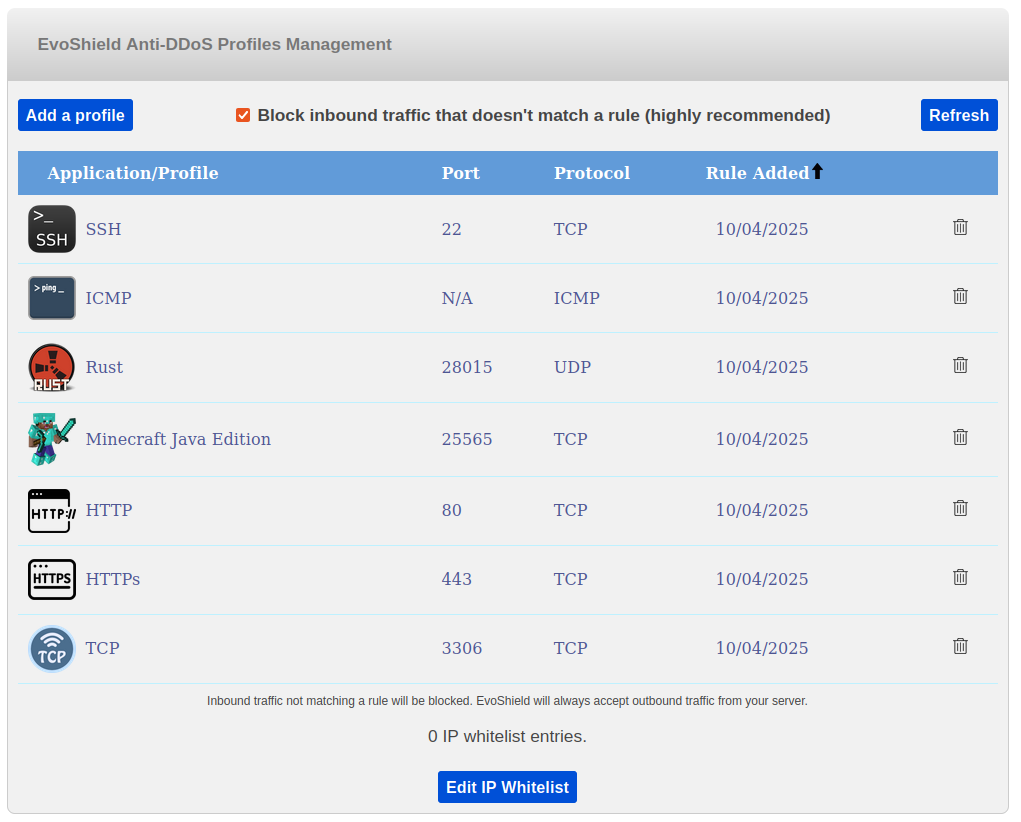
In the next example, the SSH, OpenVPN and Wireguard servers will be available for all users to connect to. If the VPN servers are used by client devices performing tasks such as browsing the internet and connecting to game servers, this configuration ensures a very high level of protection since outbound traffic being forwarded from the VPN server to the internet will be authorised automatically, but DDoS attacks taking place against the 3 authorised ports or any other port on the server will be mitigated.
For an additional layer of security, you may prefer to use the IP whitelist facility to accept traffic only from specific IP addresses. View the EvoShield IP Whitelist documentation for additional information.
Advanced Configuration (Additional Ports)
Some applications use extra ports in addition to their main port to provide secondary functionality, such as game servers with a separate query port. When setting up an EvoShield profile for an application that requires more than one TCP and/or UDP port, you will see an “Advanced Options” button which can be used to customise the port configuration.
In most cases, you do not need to change any of the port numbers for the additional ports. However if you have configured your application to listen on additional ports which are not the default ports normally used by the application, or if you are setting up a second instance of the same application and therefore need to avoid port conflicts, you can click Advanced Options and customise the corresponding port numbers.
Frequently Asked Questions
How can I find out which ports my applications are using?
If in any doubt, we recommend starting up all of the server applications that you plan to run. You can then run the following command on the server to produce a list of the ports and protocols which the applications are binding to/listening on:
Linux: sudo netstat --tcp --udp --listening --numeric --programs
Windows Command Prompt (running as Administrator): netstat -aobn
You can ignore applications which are listening on 127.0.0.1 or ::1. We recommend adding an EvoShield profile for applications listening on TCP or UDP ports on the server's public network interface.
What if I need to protect an application that is not listed?
If we have not yet developed an EvoShield DDoS protection profile for your application, you can instead use one of the more generalised profiles depending upon which protocols your application uses. This could include the TCP, UDP, SSL/TLS, HTTP or HTTPs profiles as applicable to your application or use case. For example, if you are developing a game server application which uses the UDP transport layer protocol for communications over the network between the players and the server, and the server is listening on UDP port 7777, you could then setup an EvoShield UDP profile on port 7777.
If your application is not currently listed, please contact us to submit a feature request. We are always looking to expand the range of fully supported applications.
Get EvoShield Remote DDoS Protection